Introduction: Why Zero Trust Security Is the Future of Cybersecurity
Traditional security techniques can no longer protect companies from today’s interconnected world as the most powerful and organized cyberattacks are ever ready to hit the system. Organizations require new and reliable methods to secure their data and systems as cloud computing, mobile devices, and remote work settings become common. Enter Zero Trust Security Models, a revolutionary approach that challenges conventional methods and promises higher protection.
But still, the question is, what is Zero Trust? The three main concepts of this security framework are verified, limited, and automated. So, the Zero Trust model is the idea of constantly verifying and never trusting anyone, whether inside or outside the organization. The Zero Trust model assumes that attacks may originate from inside and outside the company, in contrast to traditional approaches concentrating on protecting the network’s boundaries. It requires continuous verification, validation, and update before access to resources is granted. Businesses can guarantee that only authorized workers and devices can access important data. Implementing zero-trust security is essential for defending against emerging cyber threats.
This comprehensive cybersecurity strategy highlights an identity-driven, data-centric security architecture incorporating zero-trust security ideas. This article will cover the main features of Zero-Trust security, its advantages, method of implementation. In addition to comparison to more conventional security models.
What Is Zero Trust Security? Exploring the Fundamentals
The Zero-Trust security framework’s fundamental principle is never to trust in anyone, whether from within or outside the organization. Once someone has access to the network, they can move freely throughout the system without restrictions under a standard security structure. In a zero-trust architecture, each access request is checked, validated, and continuously monitored. It ensures it originates from a reliable source.
Key Principles of Zero Trust Security:
- Continuously Validate Access Request: Every access request to resources, internal or external, is verified and approved according to context, device, and identity.
- Use Least Privilege Entry: This approach ensures that users are only given the permissions necessary to perform their jobs by granting access to sensitive data additionally to the systems.
- Continuous Tracking: To identify unusual behaviors or illegal access, activities must be continuously tracked, recorded, and observed while offering real-time threat detection and working behavior analysis.
- Data-Centric Privacy: This approach prioritizes protecting confidential data over securing boundaries or standards. It also guarantees that data is safe even in the unlikely scenario that attackers can penetrate the network.
How Does Zero Trust Work?
A Zero Trust security model analyzes devices and users according to a range of standards, including:
- Identity: Cross-verifying the identity of access with the assigned authoritative person to ensure the user is the one who claims to be.
- Devices health: Verifying that the gadget is updated and secure.
- Behavior: Monitoring user and device behavior to spot anomalies.
- Context: Considering the location, time, and resource type being accessed.
These verification layers ensure the system is secured by additional security, even in the unlikely scenario that one layer is affected.
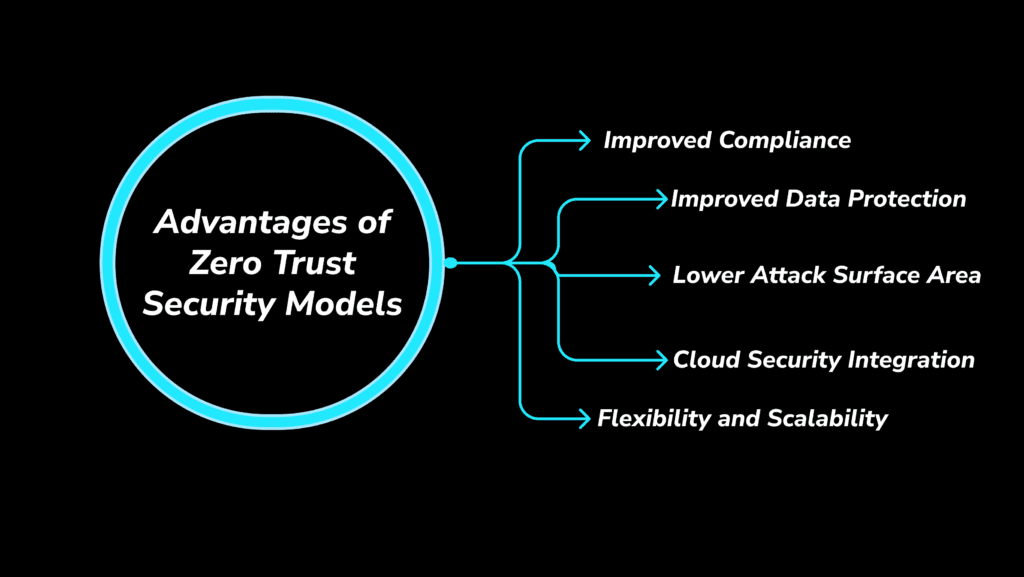
Advantages of Zero Trust Security Models: Why Companies Need Them
The limitations of traditional security models, which mainly depend on strong risk protection, have led to the development of zero-trust security solutions because of internal and external security. Are needed. As cyber threats grow more complex and attackers look for ways to get into internal networks, zero-trust security offers several benefits.
Key Benefits:
- Improved Data Protection: Even if an attacker penetrates the network boundaries, sensitive data is continuously monitored and protected using zero-trust data protection principles.
- Lower Attack Surface Area: By limiting access to network resources to confidential and technical persons, the Zero Trust design makes it far more difficult for attackers to move deep through the network.
- Cloud Security Integration: A security framework that can protect data in both on-site and cloud settings is necessary, given the growth of cloud computing. Zero Trust security is ideally suited for cloud computing security architectures, offering seamless protection across multiple platforms.
- Improved Compliance: With its robust monitoring and audit capabilities, Zero Trust compliance helps businesses meet industry regulations and avoid costly breaches.
- Flexibility and Scalability: Zero Trust security models adapt to dynamic IT environments, supporting remote work and scaling as the organization grows.
Real-World Example:
A financial services company implemented Zero Trust security solutions to protect sensitive customer data. They ensure that even if attackers can access the network, they cannot access or change the essential data archived in the cloud using a data-centric security strategy. This proactive approach significantly reduced their vulnerability to data attacks.
What’s the Difference Between Traditional Security and Zero Trust?
The network boundary is the main focus of traditional security strategies. A user or device is usually trusted to have unrestricted access to various systems once they access the internal network. However, risks are involved, especially as remote work and cloud computing gain popularity. On the other hand, zero trust security principles believe that no one, not even trusted insiders, should be taken for granted. Regardless of where the user is, it guarantees that each access request is constantly checked and verified. The two models are contrasted here:
1- Traditional Security:
- Relies on perimeter-based security.
- Once inside the network, users have broad access.
- Primarily focuses on firewalls, VPNs, and intrusion detection systems.
2- Zero Trust Security:
- Regardless of location, it assumes no one is trusted by default.
- Every access request is validated, authenticated, and authorized.
- Emphasizes data-centric security and behavior analytics to detect potential threats in Real-Time.
3- Why the Shift?
Zero-trust security is becoming more reliable and flexible as cyber attackers use advanced strategies like ransomware, malware, and phishing. Verifying each access request, reducing the possibility of attackers moving deep into the system, and protecting critical data overcome the drawbacks of the traditional security model.
Implementing a Zero Trust Security Framework: Best Practices
Zero Trust architecture requires careful planning, clear strategies, and tools. Businesses must continue these best practices to adopt a zero-trust security framework successfully:
- Analyze Your Existing Security Status: Evaluating your existing security status before implementing Zero Trust security is essential. Determine any gaps in data protection, current vulnerabilities, and places requiring updating security rules.
- Define and Classify Your Resources: Determine the systems and data that require encryption. Prioritize sensitive data and ensure that only authorized persons are given access by the least privilege principle.
- Implement Multi-Factor Authentication (MFA): Incorporate multi-factor authentication into your Zero Trust security principles. MFA ensures users cannot access critical resources with just a username and password.
- Apply Least Privilege Access: Limiting the minimum number of user permissions is necessary to lower the possibility of hacking and illegal access.
- Use Micro-Segmentation: Segment your network into smaller, isolated zones. Because of this, attackers cannot move freely even if one zone is breached.
- Adopt Cloud-Native Security Solutions: Cloud security solutions compatible with Zero Trust security models should be connected. Implementing zero-trust security throughout your IT infrastructure is essential as cloud-based apps and data become more prevalent.
- Real-Time Thrack Detection with Continuous Monitoring: Take control of threat detection by monitoring user behavior and web traffic using advanced analytics. Block any possible attack immediately if something unusual appears.
Addressing Zero Trust Security Challenges
Although the Zero Trust security framework has many advantages, businesses may encounter difficulties implementing it.
Common Challenges:
- Implementation Complexity: Integrating Zero Trust architecture with old and outdated systems will be difficult, time-consuming, and complicated. It requires multiple factors like updating security protocols and training employees.
- Financial considerations: The practical implementation and integration of Zero Trust security solutions can require significant funds. They need to modify the infrastructure and require some tools and training.
- Cultural shift: Workers could find accepting new security guidelines and procedures complex and difficult to adopt. Training and awareness programs are essential.
Solutions:
- Leverage Automation Tools: Use automation to simplify the deployment of Zero Trust security solutions and reduce complexity.
- Scalability: Choose solutions that can scale as your organization grows and adapts to new challenges.
- Train Workers: Training programs, along with awareness campaigns, are essential to guarantee a seamless shift to a zero-trust security model.
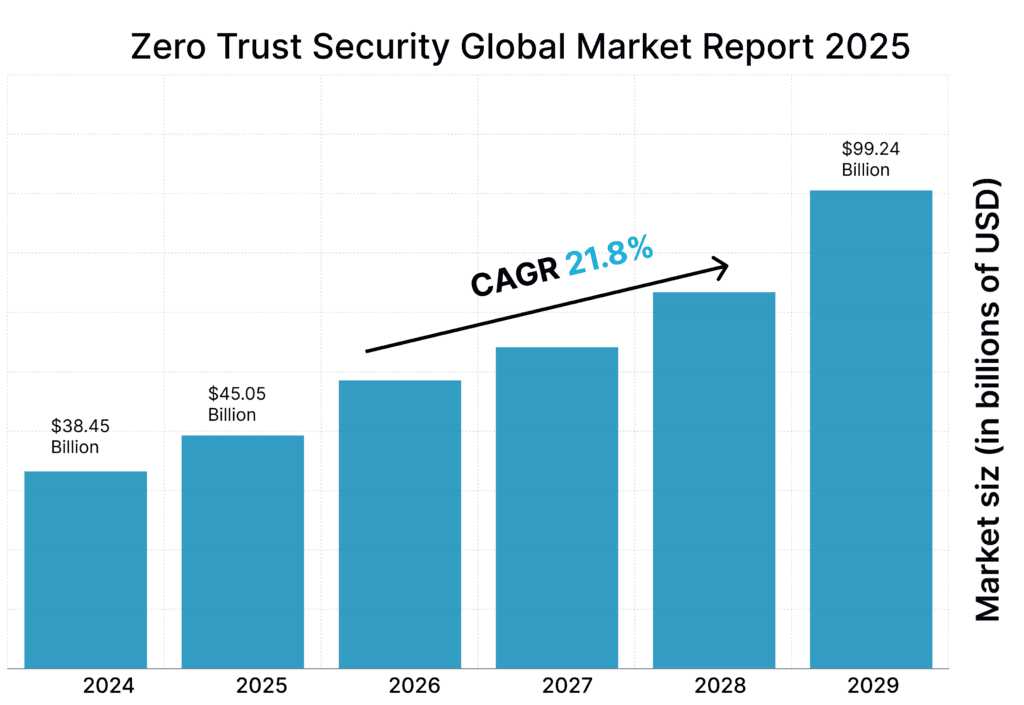
What will the Future of Zero Trust Security Models be?
The Zero Trust security approach is becoming increasingly popular as a vital part of modern cybersecurity plans. As cyber threats change, zero trust will become more and more essential to securing companies.
Upcoming Predictions
- AI and Automation: By integrating AI, threat detection will become more accurate and quick, increasing the efficacy of Zero Trust security.
- Zero Trust for IoT Gadget: As the Internet of Things (IoT) expands, linked device security will depend on the Zero Trust framework.
- Blockchain for Cybersecurity: In zero-trust security models, blockchain technology may improve data transparency and reliability.
- Cloud-Centric Protection: Zero Trust security solutions will develop to better connection with cloud infrastructure as more businesses proceed to the cloud.
Conclusion: Embrace Zero Trust Security for a Safer Future
The implementation of zero-trust security frameworks has significantly changed organizational approaches to cybersecurity. Companies can successfully defend their systems and data from emerging digital threats by using cutting-edge technologies like blockchain and artificial intelligence, adopting the Zero Trust security architecture, and applying the least privilege access rules. Whether you are a small company or a large international firm, you need to embrace the Zero Trust environment to survive in the digital advancing world.
Companies that want to remain safe in the constantly evolving digital environment must put effort into implementing Zero Trust architecture. Zero trust security provides a complete and flexible solution, whether you’re protecting against cyberattacks, guaranteeing regulation, or protecting sensitive data.
Read Also: Messaging Security Agent: Safeguarding Your Communications
Call to Action:
Secure Your Future; Implement Zero Trust Security Now!
Don’t wait until a digital attack hits your data; take action today! Strengthen your defenses, protect sensitive information, and ensure privacy rules with industry standards by adopting Zero Trust security solutions. Act immediately to prevent future damages; adopt the Zero Trust model and secure what matters most!